In the last decade, digital security has become one of the top concerns for everyday internet users. According to a 2019 survey by Statista, over a thousand Americans expressed their worries about data privacy for mobile users in the United States. The respondents highlighted “stolen passwords” as a significant concern, with 64 percent of responders, while “identity theft and fraud” ranked even higher at 72 percent.

With these compelling statistics, it’s evident that strong and secure user identification is a key factor in today’s digital world. Single Sign-On (SSO) has emerged as the solution to this challenge, simplifying the login process and offering an extra layer of security. This article aims to explain the concept of SSO in plain English, covering its workings, commonly used identification methods, and the associated advantages and potential issues.
Single sign-on (SSO) is a simple authentication method that helps users access different online services using just one set of credentials. Instead of having to create and remember separate logins for each product or service, SSO simplifies the process by allowing users to use a unique combination of credentials to access various applications seamlessly.
The underlying concept of SSO revolves around establishing a reliable identity provider (IdP) responsible for authenticating the user’s credentials and issuing a token to the application upon successful verification. This token contains the necessary permissions to grant access to different service providers (SPs) without the need for additional identifications.

When a user attempts to log in to an application integrated with SSO, they are redirected to the identity provider for validation. The third-party provider verifies the user’s credentials and returns the token to the application, confirming or denying access based on the information within the token. This streamlined process ensures efficient and secure access to various services without the burden of managing multiple login credentials.
As an example, imagine you work for a company and as part of your tasks you need to access different applications and services. With SSO, you just need to log in to your SSO company account and easily access all the applications needed without having to remember the username and passwords for each of them.
Let’s use an analogy to understand the concept: imagine the SSO is the equivalent of a master key that opens all the doors of a hundred bedroom hotel building. Traditionally, you would need a unique key to open each room; but it may happen that there is a “master key” that opens all the rooms for the cleaners and other staff members to access them easily. Just like having a hundred keys may be a hussle, remembering the username and password of all the applications an average user handles daily can be overwhelming.
The SSO does the same as this master key that opens all the hotel rooms. With the master key, you can unlock and enter any room without the burden of carrying plenty of keys; the SSO allows you to log in only once with a set of credentials (usually a username and password) and then access a set of applications for a period of time or until you log out.
There are three popular SSO authentication methods, namely SAML, OAuth, and OpenID Connect. Let’s discover in plain language what these technical concepts mean.
Imagine you are invited to a conference. Before you step in the conference center, you may need to identify yourself by checking in at the entrance.
Security Assertion Markup Language (SAML) works similarly in the digital world. It’s an entity that asks the Identity Provider (IdP) for the authentication data and sends it to the Service Provider (SP). So, the SP acts as a gatekeeper and assures you are who you claim you are by asking the Identity Provider. The IdP confirms who you are and provides a signed SAML acceptance validation.
Imagine you go to a gym near your place, and to access it, you have a badge that gives personalized access. Now imagine you forget the access card but still have your mobile phone with you. Rather than providing the badge, you can use a gym membership app provided by your company that the gym trusts. This is how OAuth works.
So, OAuth gives you access without revealing your real credentials. When you grant access to a third-party application, you authorise the application to access specific data on your behalf. To achieve this, OAuth involves three main players: the Resource Owner (you), the Client (the third-party application), and the Authorization Server (which grants access tokens). The Client requests permission from the Authorization Server to access your resources, and upon approval, it receives an access token, acting as your digital membership card. The Client can then use this access token to access only the specific resources you authorized without needing your login credentials. This way, OAuth ensures secure data sharing between applications while preserving your privacy and security.
Imagine you have a magical key that unlocks multiple doors, each leading to a different experience tailored just for you. This magical key represents OpenID Connect — a user-friendly extension of OAuth for Single Sign-On (SSO). With OpenID Connect, you not only gain access to different applications but also receive information about yourself from a trusted source.
When you log in using OpenID Connect, the identity provider (IdP) acts as your magical keyring, securely holding your identity information. It helps you gain access to various services (the doors) without revealing your personal data to each service provider. Additionally, the IdP shares relevant information about you, like your name and email, with the service providers as needed. This way, OpenID Connect simplifies the SSO process while ensuring that your personal information is protected.
Single sign-on can be implemented as a standalone verification technology or it can be integrated with a login method to smoothen the process and increase security. In the following section, we will see the most compatible methods that are combined with the SSO technologies.
Login is a process where applications and digital services validate the authenticity of a given user; SSO is a versatile approach to login using the same credentials across multiple platforms. The previous authentication methods combined with SSO create a seamless experience, increase security, and improve the overall user experience.
Having to remember multiple credentials for each application it’s a burden for users that have tens of accounts in different online platforms. The SSO is a unique approach to having only a single username and passwords, saving time and reducing the frustration of having to note down or remember all the logins. This seamless experience improves user satisfaction and generates an engagement and fidelity towards the online services.
SSO combined with an extra layer of security such as two-factor authentication (2FA) or multifactor authentication (MFA) provides a strong powerhouse to secure all your digital accounts. Having one strong password eliminates the need of remembering dozens of combinations and leads to better security.
When an employee joins a company and needs to access all the applications for their day-to-day, SSO simplifies the onboarding. With only a set of credentials, the employee can access all the apps. Similarly, when the employee leaves the organization, access to all services can be revoked with one single login.
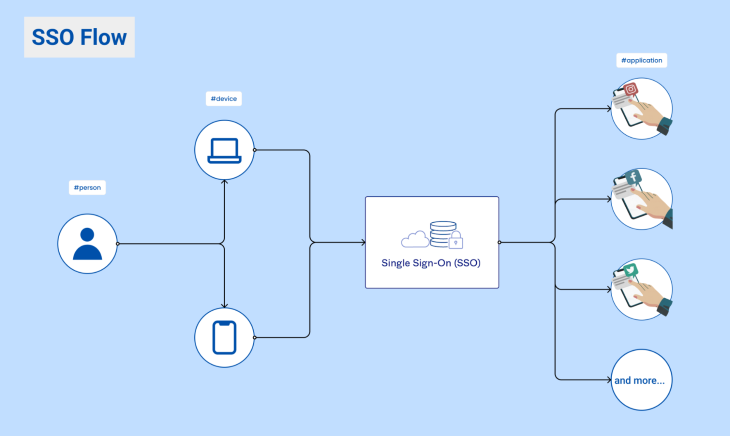
Let’s go over how SSO works step-by step so you can see how easy it is. This is how you can create a SSO flow with good UX and keep users happy.
The user navigates and opens the application with a website and its web browser or a mobile application.
The application detects the user is unauthenticated and redirects them to the SSO identity provider.
On the SSO website, the user is presented with various login options to authenticate. Typical login options are:
In this step, if two-factor authentication is enabled, the user needs to verify its identity by entering a secondary piece of validation. For example, a one-time login or opening an application used to validate identities.
The identity provider used by the application validates the credentials though its own system or with a third-party provider.
After approving or rejecting the credentials provided by the user, the provider generates an authentication token containing the key to give access to the application.
The SSO provider redirects the user back to the original application, passing the authentication token as a parameter in the URL.
The application gets the token and validates it for security and accuracy.
The user gains access to the application and the status changes to logged in.
While the user is logged in, the application may use token refresh any time to extend the user’s authentication without needing to repeat the login process from time to time. There are applications that request a new login if there is a period of inactivity or after a certain time.
If the session logs out or finally expires for inactivity or time exceeding, the user is redirected to the SSO login for reauthentication.
The single sign-on method has become a popular and streamlined approach for companies looking to implement a secure login solution. Security and identity theft are a major concerns for users, and SSO has become a valuable ally in addressing these issues. SSO streamlines the login process, enabling users to access multiple services with a single set of credentials. SAML, OAuth, and OpenID Connect stand out as popular and trusted SSO protocols. Combining SSO with 2FA, social logins, or passwordless options enhances security and the overall user experience.
The UX behind single sign-on simplifies login by granting users access to multiple services using a single set of credentials. It streamlines authentication, reduces password management burdens, and enhances security through optional Two-Factor Authentication (2FA). SSO ensures a consistent user experience, making onboarding and offboarding seamless. Overall, SSO prioritizes convenience and security, thereby improving user satisfaction and efficiency in accessing various applications.
Header image source: IconScout
LogRocket's Galileo AI watches sessions and understands user feedback for you, automating the most time-intensive parts of your job and giving you more time to focus on great design.
See how design choices, interactions, and issues affect your users — get a demo of LogRocket today.

Security requirements shouldn’t come at the cost of usability. This guide outlines 10 practical heuristics to design 2FA flows that protect users while minimizing friction, confusion, and recovery failures.

2FA failures shouldn’t mean permanent lockout. This guide breaks down recovery methods, failure handling, progressive disclosure, and UX strategies to balance security with accessibility.

Two-factor authentication should be secure, but it shouldn’t frustrate users. This guide explores standard 2FA user flow patterns for SMS, TOTP, and biometrics, along with edge cases, recovery strategies, and UX best practices.

2FA has evolved far beyond simple SMS codes. This guide explores authentication methods, UX flows, recovery strategies, and how to design secure, frictionless two-factor systems.